INTRODUTION TO TELNET
Telnet is a service which straight call the distant computing machine resources and services. Telnet service is provided with the aid of cyberspace. Telnet is a protocol that is based on client-server theoretical account. It is based on dependable, connection-oriented. TCP ( Transmission Control Protocol ) is used to set up connexion. TCP port figure is 23.Telnet was developed in 1969. Telnet is chiefly used for distant login. It establishes a nexus between computing machines that enable users to utilize a service or package installed on the distant computing machine merely as if it was installed on their ain computing machine.
Telnet is a tool that is used to entree the systems or waiters remotely, but in today life telnet is replaced by SSH ( Secure Shell ) because SSH is more unafraid than telnet. Telnet protocol is non cover the aiming onslaughts.
TCP usage Port 23 was to targeted port for onslaughts. All types of traffic onslaught about 17 % of onslaughts were directed at Telnet.
In the TCP / IP web, there are two applications in distant login map:
( 1 ) Telnet provides distant entree applications and about every TCP / IP executions provide this map. It can run on different runing systems of hosts. Telnet apply the dialogue mechanism between client – waiter procedure to find the communications characteristics available to both sides.
( 2 ) Rlogin is originated from Berkeley Unix. It merely works in the Unix systems which is now available on other runing systems.
In Telnet footings, your ain computing machine is called “ local computing machine ” , and another computing machine is called “ distant computing machine ” . When we use distant login so the user can instantly utilize all resources which are available on the distant computing machine.
3.1 Use OF TELNET:
Telnet is really easy to utilize. It is by and large composed of the undermentioned three stairss:
( 1 ) Runing Telnet client side bid initializes the session.
( 2 ) strike harding login ID and watchword.
( 3 ) Closing the sessiong after operating.
Telnet have two runing manners: input and bids. However, users interact with Telnet merely on the unfastened or closed session in most instances and chiefly as input and remote operating system or plans.
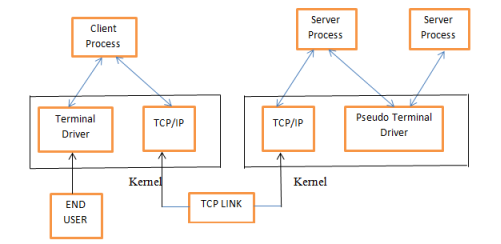
Fig.3.1 Client-Server theoretical account of Telnet
Method of Runing Telnet Plan: –
Use Telnet plan when the distant connecting. There are two ways to run the plan: The first method run the Telnet plan, the 2nd method input the bid name Telnet. First enter the Telnet province.
( 1 ) Runing the Telnet plan, the first input bid name and want to link the distant Machine’s reference. Format: telnet host name / IP reference.
Telnet bids:
| Command | Explanation |
| Open | Connect to remote computing machines |
| Set | Puting operating parametric quantities |
| Status | Display position information |
| Display | Display runing parametric quantities |
| Stopping point | Near the Connection |
| Manner | Changes to the manner line signifier or character |
| Sents | Send particular characters |
| QUIT | Exit TELNET |
Table 1: 3.1 ( telnet bids )
Wayss of Discontinuing Telnet Plan: –
There are two ways of discontinuing telnet plan. If you have connexions with the distant machine and issue by conventional methods, telnet automatically issue. Or, in
the “ telnet & A ; gt ; t ; ” prompt, recorded discontinued bid quit.
Use Telnet entree to other TCP / IP services: –
Telnet uses port 23 to accomplish its chief map, Telnet devil can besides supervise and react to other TCP ports. This characteristic can be used Telnet to link to other TCP / IP services. Tablea…? lists some of the available Telnet entree to the TCP / IP services utilizing the TCP port.
3.2 PRINCIPLE OF TELNET:
Telnet protocol provide a general, Bi-directional, character-oriented communicating installation. This protocol may utilize for terminal-to-terminal and process-to- procedure communicating.
Telnet is based on three thoughts:
- Concept of NVT ( Network Virtual Terminal )
- Principle of Option Negotiation
- Symmetric position of terminuss and procedures
Concept of NVT ( Network Virtual Terminal ) :
A TELNET connexion consists of a full semidetached house connexion ( provided by the Host/Host protocol bed ) over which passes informations interspersed with TELNET control information. At the start if we set up a TELNET connexion so the each machine is assumed as originate and terminate at a NVT ( Network Virtual Terminal ) . A Network Virtual Terminal is an fanciful device which provides a standardised, network-wide, intermediate node representation of a terminus. It eliminates the demand for ( host ) user and ( finish ) waiter and to maintain information about the characteristics of each terminuss and terminal handling tools. There are several hosts like user and waiter they map their local device characteristics and managing conventions so that they are appear to be covering with an Network Virtual Terminal over the whole web, and each one can presume that a similar function by the different party. The Network Virtual Terminal maintain a balance between the excessively restricted and excessively inclusive where excessively restricted means non supplying plenty vocabulary to each Hosts for mapping into their local characteristic sets and excessively inclusive agencies punishing users with the modest terminuss. The Network Virtual Terminal is a bi-directional character device with a keyboard and pressman. Here pressman is used to react the entrance informations and the keyboard is used to bring forth surpassing informations which is sent over the Remote ( TELNET ) connexion and, if ECHO’s are desired to the Network Virtual Terminal pressman. ECHO’s will non anticipate to track the whole web. The codification set is 7-bit ASCII codification in an eight-bit field, with some exclusions. Any transition and timing considerations are small/local jobs that do non impact the Network Virtual Terminal.
Principle OF OPTION NEGOTIATION:
The rule of negotiated options takes awareness of the fact that many sztes wish to supply extra services over and above those available within an NVT, and that many users have sophisticated terminuss and prefer elegant, instead than minimum, service. Assorted options are provided within the TELNET protocol to let a user and waiter to hold upon more elaborate ( or possibly merely different ) conventions for their TELNET connexion. Options may be invoked to stipulate the character set, the echo manner, the line breadth, the page length, etc. The basic protocol for enabling an option is for either party ( or both ) to bespeak that the option take consequence. The other party may so either accept or reject the petition. If the petition is accepted, the option instantly takes consequence. If it is rejected, the associated facet of the connexion remains as specified for an NVT. Since all parties must be prepared to back up the NVT, a party may ever decline a petition to enable, and must ne’er decline a petition to disenable, an option. A bustle of option petitions is likely to happen when a TELNET connexion is foremost established, as each party efforts to obtain the best possible service from the other. Beyond that, options can be used to dynamically modify the features of the connexion to accommodate altering local conditions. For illustration, the NVT, as antecedently explained~ uses a transmittal subject good suited for line-at-a-time applications but ill suited for character-at-a-time applications. A waiter electing to give the processing operating expense required for character-at-a-time operation may ( when it is suited for a local procedure ) negotiate into character-at-a-time manner. However instead than for good burden itself with the excess processing overhead~ it may exchange ( i.e. , negotiate ) back to line-at-a-time when the “ tighter ” control is no longer necessary.
In the undermentioned, we use the illustration of repeating to actuate and exemplify the rules of option dialogue.
A basic observation to be made sing echoing is that Hosts which supply synergistic services tend to be optimized either for terminuss that do their ain echoing or for terminuss which do non, but non for both terminal types. Therefore, a set of repeating conventions which would forbid a waiter from originating a alteration in echo manner would be overly restricting. Waiters would be burdened with users who are in the “ incorrect ” manner, in which they might non otherwise hold to be, and users would be burdened with retrieving proper repeating manners.
TELNET reverberation manner dialogue is based on three premises: –
First, both the waiter and the user should be able to propose the echo manner.
Second, all terminuss must be able to supply their ain reverberations, either internally or by agencies of the local Host.
Third, all waiters must be able to run in a manner that assumes that remote terminuss provide their ain reverberations.
The last two premises result from the desire for a universal, minimum footing upon which to
Build. An execution based on these regulations has, in consequence, the undermentioned bids ( the existent bids are presented at the terminal of this subdivision ) :
– Echo, when sent by the waiter to the user, means “ I ‘ll repeat to you ” ;
– Echo, when sent by the user to the waiter, means “ You echo to me ” ;
– No ECHO, when sent by the waiter to the user, means “ I wo n’t repeat to you ” ;
– No ECHO, when sent by the user to the waiter, means “ Do n’t you repeat to me ” .
Whenever a TELNET connexion is opened between a user and a waiter, both user and waiter must presume that the user is repeating locally. If the user would prefer the waiter to bring forth reverberations, it can direct the waiter an ECHO bid. Or, if the waiter would prefer to make its ain echoing, it can direct the user an ECHO bid. The receiver of an ECHO bid is non required to alter the manner it handles repeating, but it may hold to react to the bid. If the requested manner of operation is acceptable, the receiver begins runing in that manner ; if “ get downing ” means altering from a old manner, the receiver must besides react with the ECHO bid to bespeak that ( and when ) the conversion took topographic point. If the requested manner of operation is non acceptable, the receiver must react with the bid ‘s opposite to bespeak its refusal ( this must be NO ECHO. since neither party is allowed to decline a alteration into NO ECHO ) .
Working Procedure:
Remote login followed the client – Server theoretical account. Using the Telnet protocol for distant login are required to run into the some necessary conditions: The understanding contains the Telnet client plan which installs on the local computing machine and cognize the distant host IP reference or sphere name and must cognize the login ID and watchword. Remote login procedure work as follows:
( 1 ) The local machine is linking to the distant host. The procedure is really a TCP connexion ; the user must cognize the distant host IP reference or sphere name ;
( 2 ) On the local terminus user inputs user name and watchword and after enter any order or characters to NVT ( Net Virtual Terminal ) format for transmittal to the distant host. The procedures send really a IP package from the local host to the distant host.
( 3 ) The distant host end product the informations NVT format which is converted into a format acceptable back to local terminuss, including input bids and bid echo the consequences ;
( 4 ) Finally, the local terminuss undo the connexion to the distant host. The procedure is the remotion of a TCP connexion. Figure 1 shows a Telnet client / waiter, a typical connexion diagram.
3.3 PROBLEM IN TELNET:
Using telnet provides many benefits and fast processing but computing machine security is chief issue in utilizing telnet.
- When we connect the system remotely it does non supply right hallmark, the individual you are connected is authorized or non, or another hacker interrupt in center or non.
- Telnet does non code the information sent over the connexion ( including watchword ) so, it is frequently practical to steal on communicating and utilize the watchword subsequently for malicious activities.
3.4 TELNET Attacks:
There are several types of telnet onslaught. Listed below are the chief onslaughts in telnet.
- Telnet communicating whiffing
- Telnet beast force onslaught
- Telnet DoS ( Denial of Service )
TELNET COMMUNICATION SNIFFING:
To procure informations communicating in a present twenty-four hours individual uses secure shell SSH because it is more unafraid so telnet and it can be configure easy in the many organisation SSH is used as default. By taking SSH in topographic point of telnet we are more unafraid. It solves the biggest security job. There are some possible onslaughts ; they can compromise with the telnet.
Encryption provides more security from the aggressors but telnet non utilize the encoding engineering. When we communicate device on remotely login so the informations send in the field text which can be entree by the 3rd party/ unauthorised users. So, that it is the large security job in telnet and to work out this we uses bid vulnerable to whiffing. Attacker can easy see the constellation and the watchword which are used by the user to link it enter in constellation manner. Once password information is get by the user, it can be used for malicious activities subsequently.
TELNET BRUTE FORCE ATTACK:
Once aggressors get the watchword they might utilize telnet protocol to remote entree on the web switch. If you configure a login watchword and set watchword to authenticated users for the entree so it provides a little degree of security to assist from the unauthorised entree. Telnet is non unafraid bur watchword for authenticate people can do it procure on the small level.it is non unafraid to vty lines but tools handiness makes secure and check the onslaughts.
BRUTE-FORCE PASSWORD ATTACK:
Once aggressors gets the watchword at the distant connexion clip, they can used it for malicious activities at the ulterior phase. There are another option to acquire watchword, hackers maintain a list of common watchwords like day of the month of birth of individual, son/ girl name and they try to set up a telnet connexion utilizing that watchword and common words in dictionary list. Attackers can pass a whole twenty-four hours on the computing machine to think the correct watchword, one time they guess right they can login the distant system and stole the users of import information like history no. etc, one time they get they use subsequently to stole money from the history.
They are smart to think the watchword, hacker who are making this they may be large interior decorator or professional coder. If they are programmer, they can compose a plan to utilize of dictionary words and seek the word inside start from A and terminal at Z. but this smarting is non plenty because people are excessively smart they set their watchword like rudiment @ 123, so to find/ conjecture such type of watchword they use combination of words, characters and symbols.
DoS Attack:
Denial-of-Service onslaught is an onslaught that targeted to forestall service entree to those persons who have legal right to it. A system compromised by a Denial-of-Service onslaught to put to death a codification that generates a figure of back-to-back petitions for a service to make a constriction in informations transmittal line and, as a consequence of this the onslaught makes the service unavailable to the legitimate users. This onslaught does non necessitate high degree of accomplishment or cognition ; it can be initiated by an person who has basic accomplishment of the capable affair. It includes Ping of decease, synchronise Sequenced Number ( SYN ) implosion therapy, spamming and smurfing.
Synchronize Sequenced Number ( SYN ) implosion therapy: It is an onslaught where answers are irrelevant. SYN-flooding requires the aggressor to continually direct a big figure of TCP SYN packages to the mark machine. When each SYN-packet received, the mark host sends an recognition package to the supposed transmitter. The mark so waits for a answer to the recognition. The aggressor ne’er sends the answer it causes the mark to go on to wait. When buffer is full so all buffers are used no farther web connexions to the mark are possible. Because of the high volume of packages sent during a SYN-flood, an attacker’s packages are more likely to utilize the buffer than a package from a legitimate connexion.
Smurf onslaught: In Smurf onslaught beginning host set finish reference and echo package message broadcast on the web. In this instance there is a big figure of answers received from the web. The construct of reference spoofing and package elaboration feats on the mark machine which are present on the web. The coveted return package non necessary for the aggressors. Echo answers send by the every one so that echo answer entree in the broadcast way.by the aggressors for successful attack..
Pinging of deepness: The maximal size package is of 65,536 eights. The Ping of decease is an onslaught sends over the outsize ICMP datagrams ( encapsulated in IP packages ) in the victim. Large systems having in the outsize package so system will crash and bring up, consequence is stored in denial of service.
WAYS TO COMPROMISE REMOTE CONNECTION
When we connect with the machine so there are so many benefits like resource sharing, usage of other computing machine from the same topographic point.
It provide high velocity to work quicker, no demand to traveling the from one topographic point to another. Telnet is a tool that is used to entree the systems or waiters remotely, but in today life telnet is replaced by SSH Secure Shell because SSH is more unafraid than telnet. Telnet protocol is non covering the aiming onslaughts. TCP usage Port twenty three was to targeted port for onslaughts. All types of traffic onslaught about 17 per cent of onslaughts were directed at Telnet.
But whatprotocoldo we use for this sort of operation? Telnet is good but less than SSH because SSH is more secure.





